What is the difference between Security tokens and Utility tokens?
The advent of cryptocurrencies has shaped the global financial system in ways never before conceived.
Today, various elements seek to cash in on this growing crypto market by introducing start-up companies and seeking funds from the public through ICOs (crowdfunding).
Some of these ICOs have been legitimate, while a host of others have been fraudulent with the intention of stealing investors’ money.
Governments worldwide have introduced measures to guard their citizens against fraudulent ICOs and schemes.
A typical example is the United States SEC which is firmly against fraudulent and unregistered token sales and ICOs.
The question is, “How do they distinguish between a fraudulent ICO and a legitimate ICO?”
The answer can be found in the token category – there are 2 major types of tokens sold in ICOs:
- Security tokens
- Utility tokens
To know their difference, we will have to discuss them in plain English, starting with “security tokens.”
What are Security Tokens?
An ICO aims to source funds to complete a project.
ICOs means “initial coin offerings”.
For a startup to generate funds in the decentralized crowdsourcing space/ICO, it has to give out a portion of its tokens to investors in exchange for their money.
For an investor to agree to part with his/her money, the start-up has to define ways in which their idea will profit them clearly.
Security tokens are categorized as tokens that promise to:
- Share profits
- Pay dividends
- Pay interest
- Invest in other tokens or assets
- To generate profits for their holders
An ICO that sells its tokens to investors with the promise of investing their money to pay them dividends, profits, interest, etc., provides securities.
Tokens of this nature are prohibited in countries like the United States.
Even when allowed, it must be registered with the SEC before being sold.
This is after scrutiny and confirmation that SEC standards for Security tokens are met.
However, with the search for the next big project yielding millions, many founders and start-ups have become unaware of how to launch security tokens.
They sometimes get to launch them without the knowledge of the SEC, a move that has led to the recent crackdown on unregulated ICOs and tokens by the United States government.
The question is, “How do you know if a token is a security token?”
To know whether or not a token is a security token, you have to subject it to a litmus test called the “Howey Test.”
“A Howey Test is a test created by the Supreme Court for determining whether certain transactions qualify as investment contracts.
Under the Securities Act of 1933 and the Securities Exchange Act of 1934, those transactions are considered securities and therefore subject to certain disclosures and registration requirements.”
A security is found to exist when all four of these elements exist:
- Investment of money
- In a common enterprise
- With an expectation of profits
- From the efforts of others.
Therefore, to legally launch an ICO that offers “security tokens,” you need to follow the procedures/rules of the SEC.
Furthermore, it is important to note that the United States SEC is not totally against ICOs; it is against unregulated ICOs and security tokens.
Security tokens like Polymath and tZERO are currently regulated by the SEC, hence why they are allowed to operate.
What are Utility Tokens?
Unlike security tokens, utility tokens power the decentralized projects or applications a team tries to build or raise funds for through ICO.
They are also called App Tokens or App Coins.
For instance, let’s say a team is trying to build an application that will allow users from all over the world to send and receive funds while protecting their identities instantly.
Every transaction on the application comes with a fee, which is to be paid with the application’s token.
At this point, the team knows what they wish to create but lacks funds.
They can source funds by offering some of their platform tokens to interested investors before launching the platform.
Here, the tokens on offer do not guarantee a profit.
Still, due to the laws of demand and supply, the tokens will appreciate when the platform is launched and eventually gain popularity.
However, many teams try to tie profit guarantees to their utility tokens in a bid to lure investors into investing in their ICO, and projects of this nature are also being closely monitored by the SEC nowadays.
So, you must understand a token’s utility, usability, and economics before investing in it.
Tokens like Ethereum, Sia, and Filecoin are classified as utility tokens.
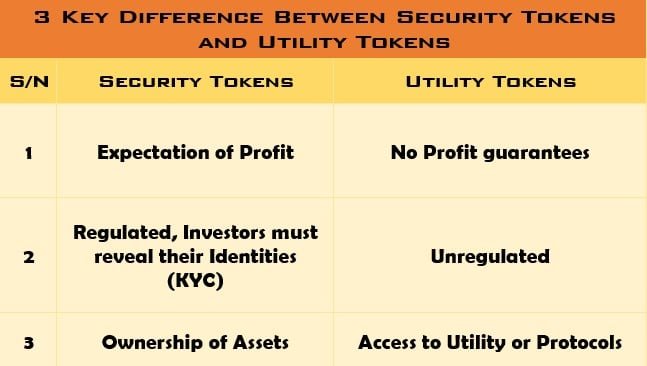
Differences Between Security Tokens and Utility Tokens
Finally, the major differences between security and utility tokens can be summarized as follows:
Conclusion
Be mindful of the ICOs you put your money on.
If you are investing in a security token – you have to understand what you are getting into thoroughly.
Furthermore, before investing in a utility token – you need to understand what the application aims to achieve.
When the platform launches and eventually fails to deliver on its promises or does not gain the required popularity, the value of the tokens will depreciate.
And so will your investment.
Finally, you must be mindful of security tokens that present themselves as utility tokens or are not duly registered to provide securities because, if the SEC catches up with their activities, your funds might never hit your account again.
Non-compliant ICOs like Tezos and Centra (CTR Token) have been closed down by the SEC, and I have a feeling that people who invested in them might never recover their funds.
Hope this review helped you understand the difference between a security token and a utility token?
Please leave your comments and opinions in the comment section below and don’t forget to share!
Thank you.



0 Comments